News
A digital Red Cross
Because the digital infrastructure of humanitarian institutions is vulnerable to cyberattacks, the team at the Centre for Cyber Trust are developing digital emblems to protect these systems.
In September of 2020, the University Hospital of Düsseldorf suffered a critical blow: a cyberattack on its servers brought the hospital to a standstill for a whole week. The blackmailers behind the malware relented when they realised they had not, as planned, hit the university itself. Tragically, the situation was resolved too late for one patient who had to be removed to another hospital—and who later died.
What exactly happened? Professor Peter Müller, co-leader of the Centre for Digital Trust at the Swiss Federal Institute of Technology Zurich (ETH Zurich) explains how these attacks work: “The malware is programmed to independently attack computers that lack sufficient protection. Often, the hackers have no real control over the attacks.” A weakness in their “business model”. Indeed, cybercriminals who blackmail firms aim to fly under the radar. A high-profile case like an attack on a hospital increases their risk of being tracked down by the authorities.

![[Translate to English:] Cyber Trust [Translate to English:] Illustration](/fileadmin/_processed_/b/8/csm_05_Digitales_Vertrauen_EN_daee7840f4.png)
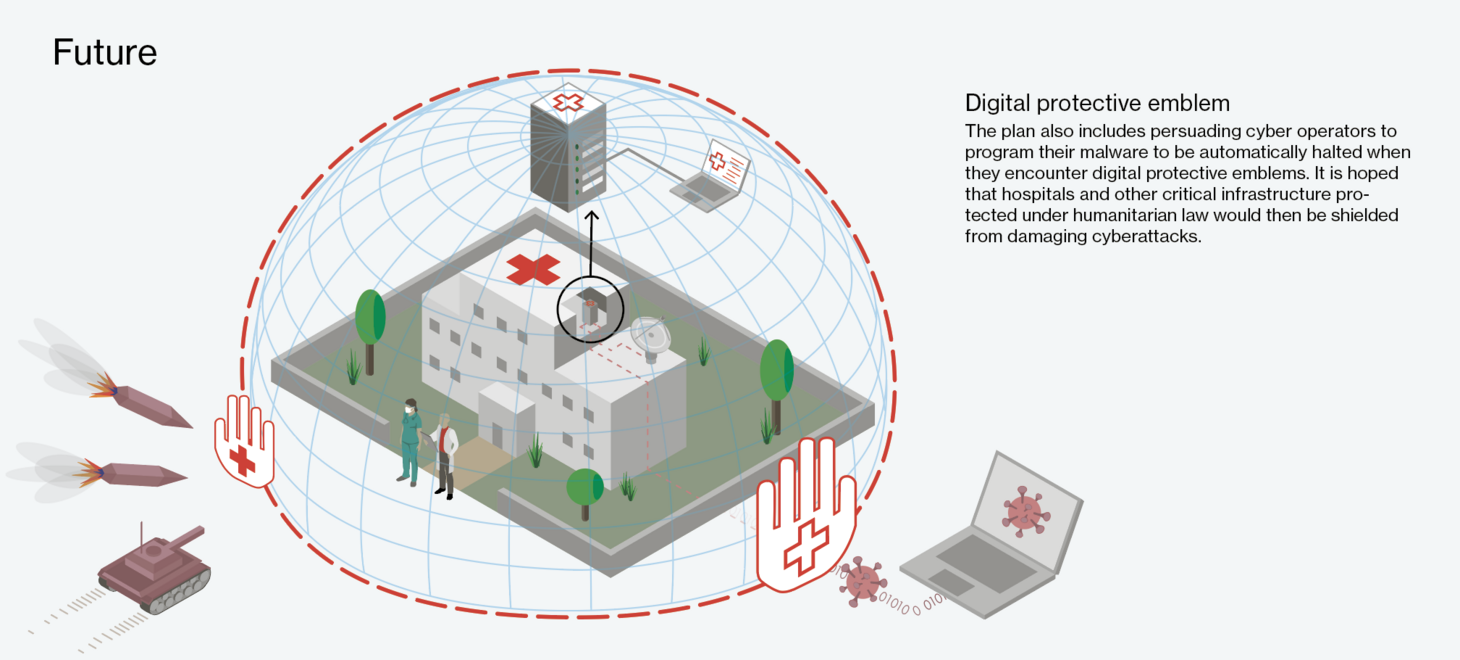
To date, the protections in place for digital infrastructure in public and humanitarian institutions like electricity works and hospitals leave them vulnerable to cyberattacks. Nor is there a digital Red Cross alerting malware programs that the targeted infrastructure is protected under international humanitarian law. Seeing the need for a digital protective emblem to act as a warning sign, the International Committee of the Red Cross approached the Centre for Cyber Trust at the end of 2020. “Just as recognised symbols show parties in armed conflicts what stands under protection, the digital infrastructure of humanitarian organisations must be made recognisable to cyber operators,” explains Professor David Basin, co-leader of the Centre.
Together with his research group, Basin has developed a concept for how such a digital protective emblem could function (see diagram). In order for an emblem to be accepted by attackers (be they nation states or criminal organisations), it must first and foremost be seen as trustworthy and impartial. But what precisely promotes or undermines the trust of these actors? This question, which considers IT security from a behavioural perspective, is being addressed by Professor Matthew Smith, the project’s research partner at the University of Bonn.
Text: Sabine Witt
Illustrations: Timo J. Walker